ZeroTier: Next-generation connectivity and cybersecurity.
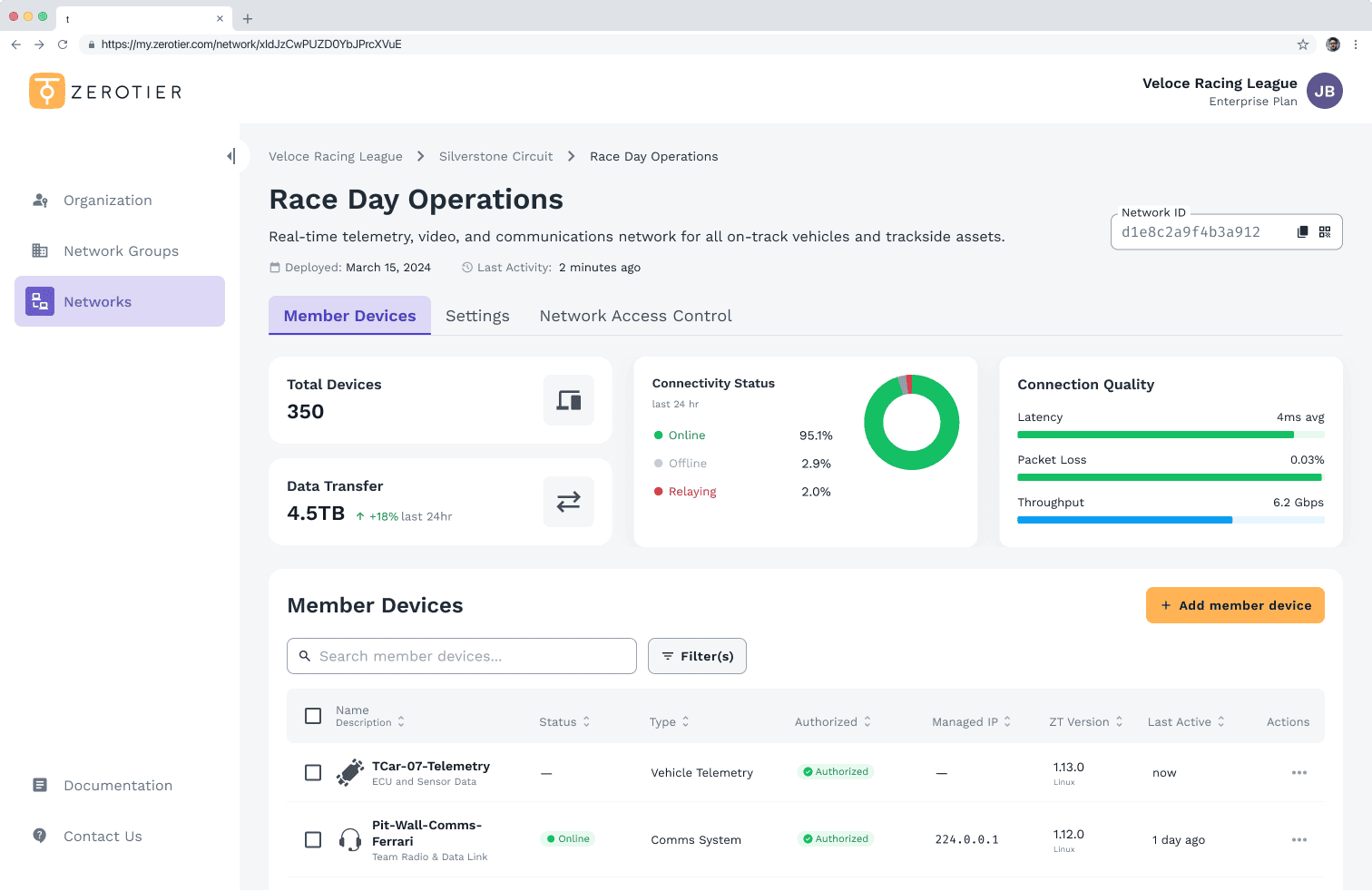

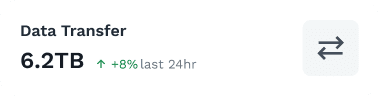
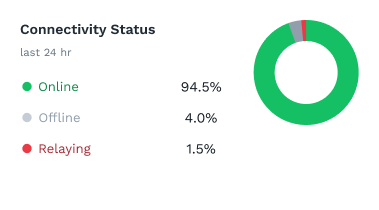
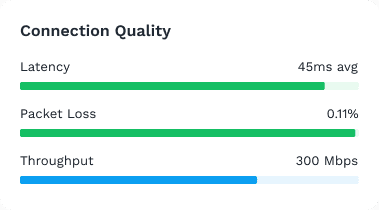


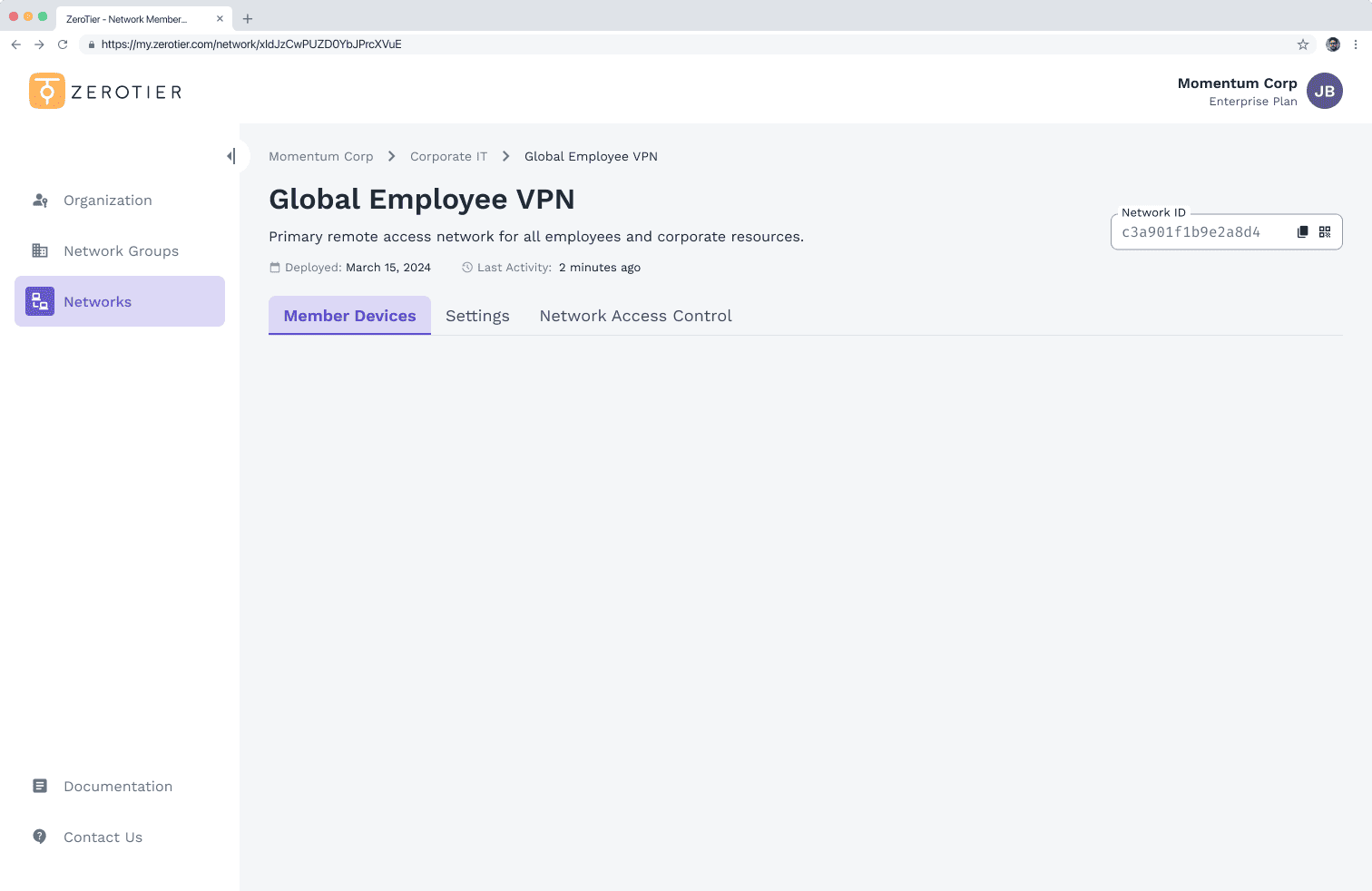
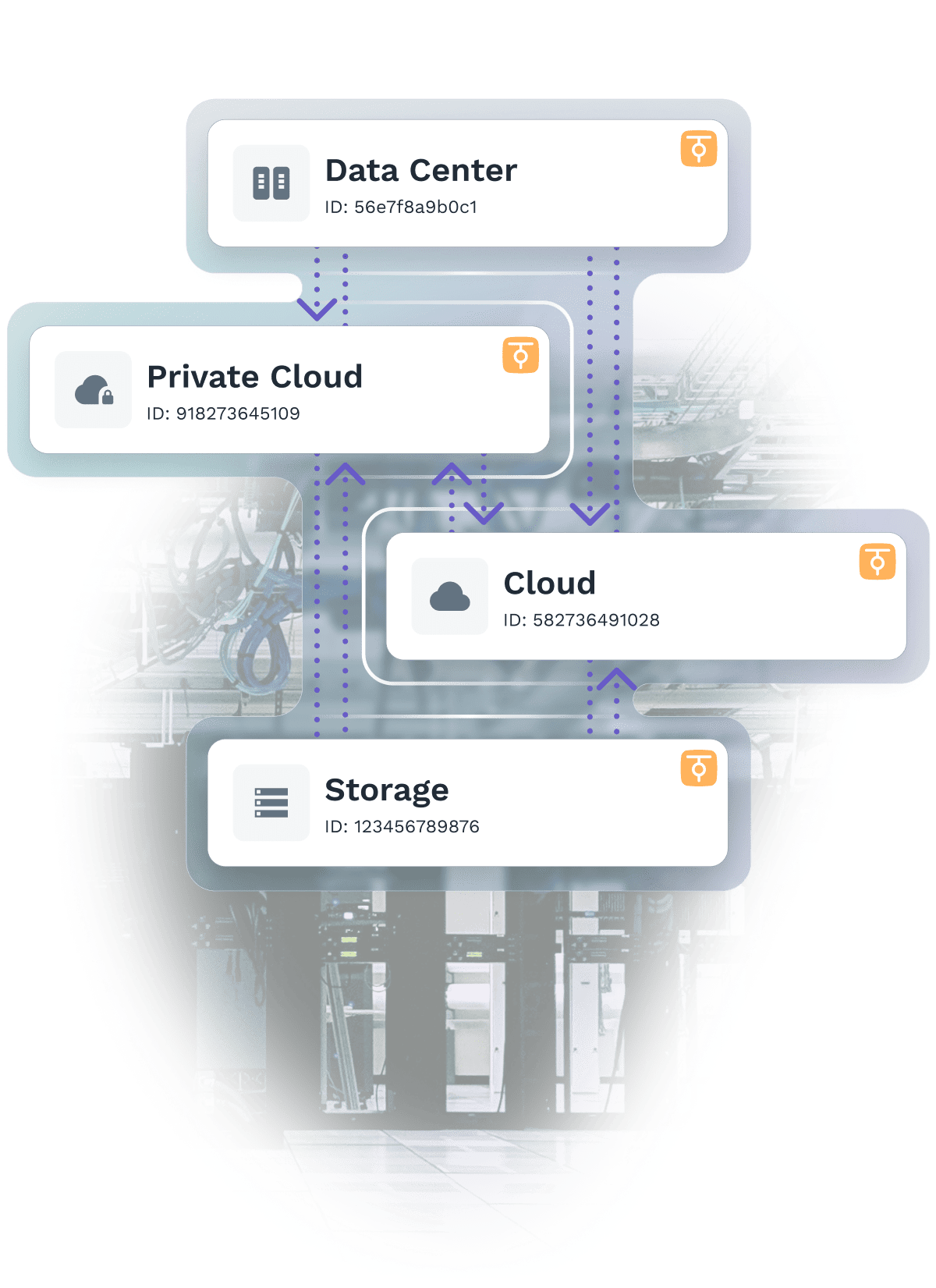
Whether you’re connecting two devices or two million, ZeroTier makes global networking easy with a software-defined networking platform you can deploy in minutes, not days.
Build, manage, and scale secure networks, without the hardware headaches.
We didn’t just simplify networking; we broke it down and built it better. No more tangled messes, just deploy in minutes and control your entire world from one dashboard. Simple isn’t a feature; it’s our operating system.
“My only regret is that I didn’t go down that path earlier — much earlier.”
— Head of Technical Operations, AI-powered Parking Provider
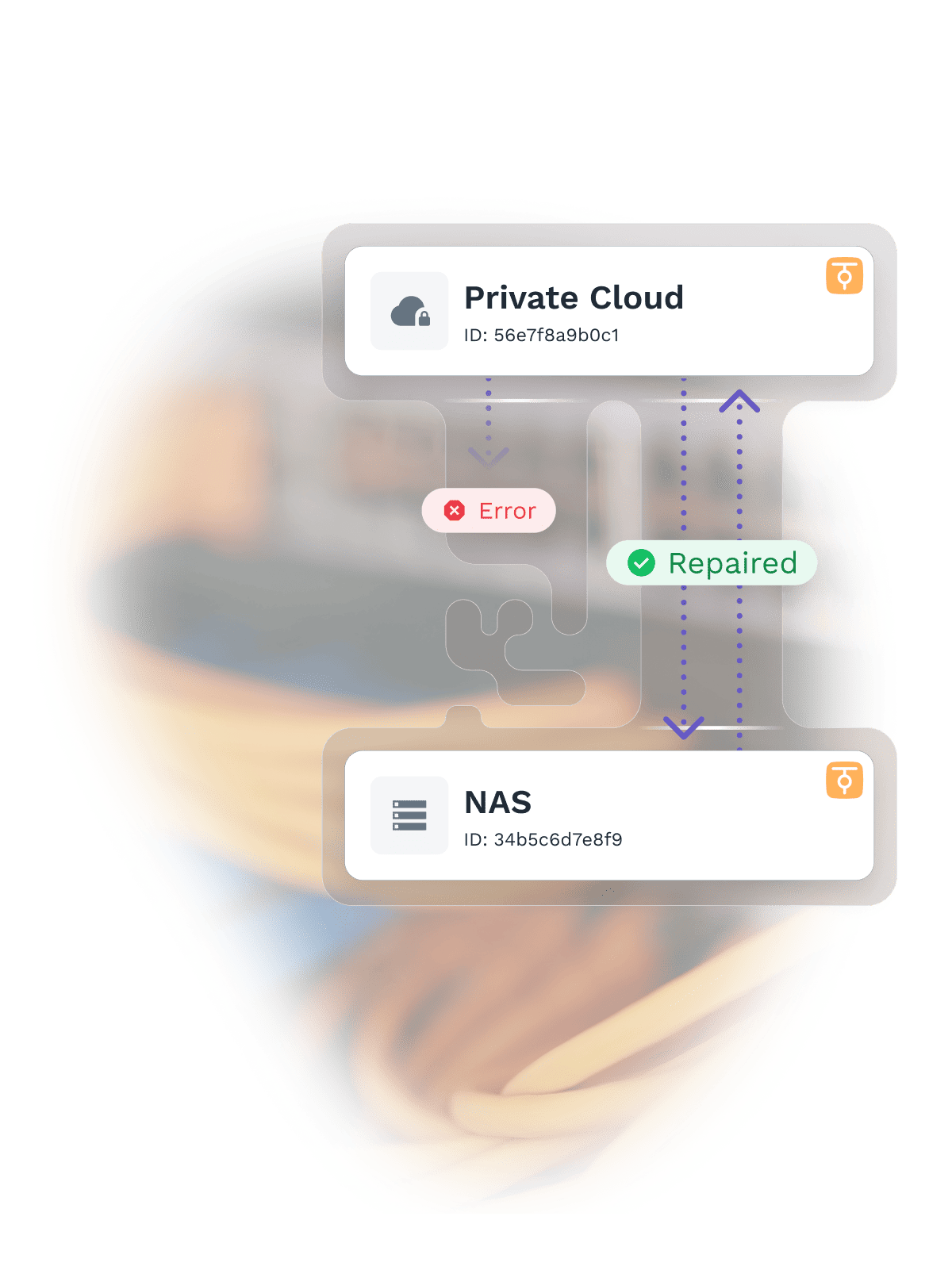
Networks break. Ours doesn’t. We built resilience into every byte, so your connections stay rock-solid, even when the world goes sideways. Hardware fails, connections drop, but your ZeroTier network just keeps going.
“ZeroTier unlocked doors for what we were capable of as a company and for our own projects.”
— Operations Manager, Smart Building Technology Provider
Other networks route your data through who-knows-where. We don’t. We put privacy and security first, with end-to-end encryption and direct connections that just work. Security isn’t a layer; it’s the foundation of everything we build.
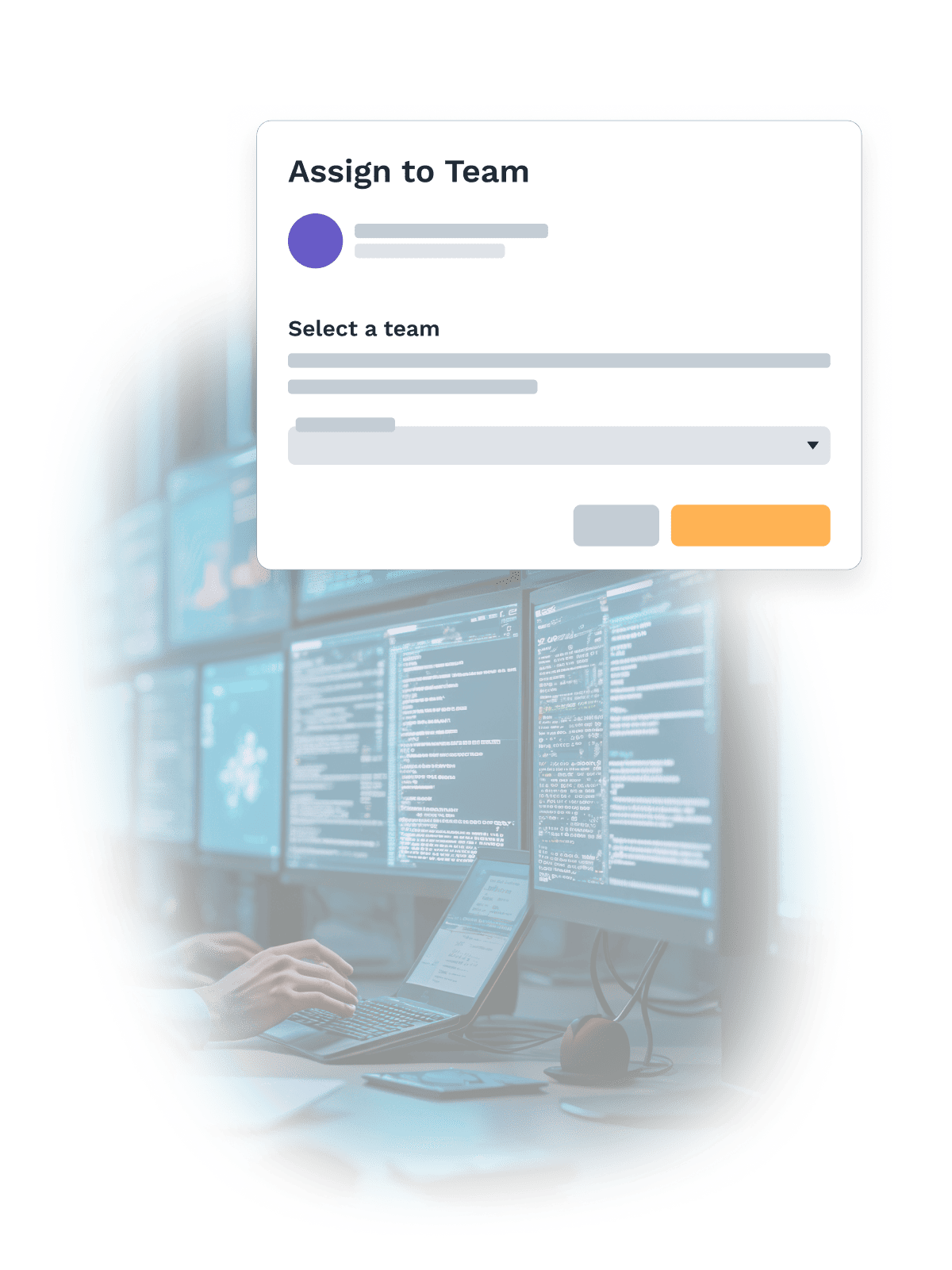
















From smart bulbs to spaceships, whether you have 10 users or 10,000, ZeroTier has an option that fits you.
For accounts or organizations created after Nov. 5, 2025.
Recommended for new users
For old accounts created before Nov. 5, 2025.
For existing users
Not sure which to choose? Contact Support.